Securing your industrial information
In today’s world, having access to information from your mobile device or home computer has become essential. This information has great value to you and some of it to other people as well. Many of us have become complacent, or simply do not consider the security of our information, as much as we should. Keeping information from industrial applications, just like your personal information, safe is a top priority. Cloud solutions for industrial information access are part of many of today’s monitoring solutions. There are a few key terms that you need to know, whether you are considering, or already have, remote access. I hope this article helps you with securing your industrial information.

Protecting your industrial information at login
Security considerations start with your sign in process, which begins with the users and usernames. To start with, you need to create individual user accounts for access. It is never a good idea to use a shared or generic account for an application that is exposed to an unsecured network like the internet. One reason is that it is hard to communicate a change of a username and/or password to a group of people, securely. This can lead to frustration for some users. Secondly, it may be a person who had access through that account that caused the breach in the first place.
You are probably getting tired of hearing that you need to use a strong password. We have discussed this in a previous blog ourselves, The truth about cloud-based solution security. Nevertheless, I cannot mention it enough. A strong password is a great form of protection.
A couple of other tactics that you may not think of are password expiration times and login attempt limits. Limiting the number of login attempts thwarts cyber threats like brute force attacks. This is where a person, or an automated system, tries to guess your login information through repeated attempts. Therefore, by limiting the number of attempts, you have effectively blocked them. By changing your password periodically, you eliminate the chance of someone being able to use your password after its expiration period.
When it comes to industrial information, encrypt everything
In a previous blog, I encouraged the use of encryption Use encryption to protect your information through Transport Layer Security (TLS). However, I really did not talk about what is required to achieve it. Therefore, I will mention that here. In order to implement TLS, the application needs a security certificate. There are two types of certificates, a self-signed certificate which is a certificate that is not signed by a certificate authority (CA) or one that is issued by a certification authority (CA) which is an entity that issues digital certificates.
The most secure certificate is one that is issued by a CA. For ours, we use a company called Digicert, formerly known as Thawte. Implementation of a certificate, for an on premise solution, can be very daunting and should only be attempted by a professional who is trained in cyber security. A cloud solution has already done this if the lock icon is showing in the address bar of your browser.
Encryption also includes the packets sent to the cloud solution. There are various means of encrypting data outside of a browser. The important thing to know is that encryption is in place, and is a key element for securing your industrial information.
Always use multi-factor authentication for your industrial information
I have said it before and will repeat it here, without multi-factor authentication you are only as good as your username and password. In a previous article, Multi-Factor Authentication is Not an Option!, I talked about the need for it, but did not go into any further details about some of the available options. So, I would like to mention a few now. The one option the article addressed was sending an identity code to a personal device, like a mobile phone or personal computer. Another form of MFA includes a user secret question. A few examples include, father’s middle name, best friend as child, or elementary school. Finally, a machine-to-machine solution would store a passphrase on each machine that allows access, and is separate from any user information.
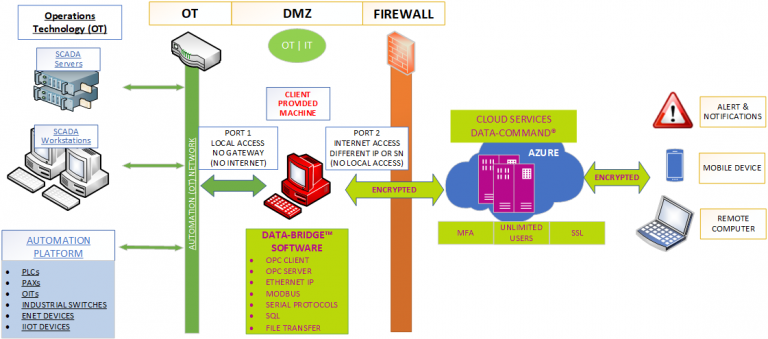
You need to create a DMZ to secure your information
There is a whole market that focuses on creating a DMZ (demilitarized zone), providers include Cisco and Barracuda. I encourage you to look at their sites, which have a lot of good information, about creating a DMZ. For your industrial application, you need to separate the Operations Technology (OT) from the unsecured network both physically and logically. Many times, clients think this is the case, but it really is not. Implementing a firewall is a good first step. Unfortunately, if not done correctly, it only gives you a false sense of security. As an example, opening up external ports is never a good idea, especially with a public static IP address. Another mistake that is commonly made, is not filtering traffic by specific IP addresses.
If you have remote access to your industrial automation information, or even worse your automation platform itself, and do not have every one of these things in place, then you are vulnerable to cyber threats.
Don’t forget about your securing your remote sites
If you are getting information from a remote location such as a water storage tank, booster station, or lift station, don’t forget to secure this information as well. Most automation, that utilize cellular technology for smaller applications, sit on a public 4G network. If the site uses a static IP Address and is public facing then you are vulnerable. However, using cellular communication is better than a public licensed radio system with no encryption.
About The Author
The President and founder of Data-Command with over 25+ years of business development, 35+ years of automation, and 40+ years of software development experience. In 2005, Data-Command was born from his passion to provide information to municipalities and industry that would have a positive impact on their operations, and he has never lost this passion.